Hi Everyone,
I just want to alert you , that Many
organizations around the world were victims of malicious “WannaCrypt” software
last week.
Seeing businesses and individuals affected by cyberattacks such as
this is painful. The Microsoft's teams have worked relentlessly over the last few days to
take all possible actions to protect microsoft users.
What is Ransomware?
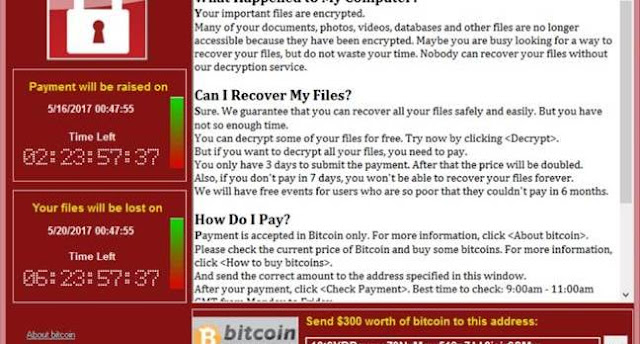
It is a cyber-attack that involves hackers taking control of all the data files or in some cases complete computer making it completely inaccessible until a ransom is paid.What is WannaCry Ransomware?
On Friday, 12 May 2017, over 200,000 computers across 150 countries including India were infected by the WannaCry ransomware attack. WannaCry is a ransomware that encrypts all the data files on the infected computers and asks users to pay 300 USD to restore the files. If the ransom is not paid in three days it threatens to double the ransom amount. This recent cyber-attack has created a global havoc and brought to light the importance of robust cybersecurity solutions for enterprises like yours.Who all are impacted or can get impacted?
This ransomware has already affected high profile organizations in Spain, UK, China and many other countries including India. These organizations include clinics, hospitals, universities, telecom, gas, electricity and other utility providers.
I humbly request to you, if you have till not attacks this malware, you are lucky, but don't takes lightly. First take backup your whole data into pen-drive or External drive and keep it out of mounted to PC after taking backup successfully.
If you using Linux Operating System, You are SAFE 😃
Here are a few things for your reference:
- If you are using
Windows Vista, 7, 8.1 & 10: In March, The microsoft released a
security update which addresses the vulnerability that these attacks are
exploiting. Those who have Windows Security Update enabled are
protected against attacks on this vulnerability.
- For those organizations who have not yet applied the security update,
i suggest you immediately deploy Microsoft Security Bulletin MS17-010.
- Activate Windows
Defender: For customers using Windows
Defender, we released an update earlier today which detects this threat as
Ransom:Win32/WannaCrypt. As an additional “defense-in-depth” measure, keep
up-to-date anti-malware software installed on your machines. Customers
running anti-malware software from any number of security companies can
confirm with their provider whether they are protected.
- If using older
version of Windows: Customers running versions of
Windows that no longer receive mainstream support may not have received
the above mentioned Security Update released in March. Given the potential
impact to customers and their businesses, we have released a Security
Update for platforms in custom support only. Windows XP, Windows 8 and
Windows Server 2003 Security Updates are broadly available for download
now (see links below).
- Additional Steps
to consider: This attack type may evolve
over time, so any additional defense-in-depth strategies will provide
additional protections. (For example, to further protect againstSMBv1 attacks, customers should consider blocking legacy protocols
on their networks). Some of the observed attacks use common phishing
tactics including malicious attachments. Customers should use vigilance
when opening documents from untrusted or unknown sources.
- Keep ON System restore: System protection is a feature that regularly creates and saves information about your computer's system files, programs, drivers, and registry settings as restore points for all drives that have system protection turned on. For Further Information click on
If you like my Blog, please write Comments.
Comments
Post a Comment